EdgeGuard: Machine Learning for Proactive Intrusion Detection on Edge Networks
Main Article Content
Abstract
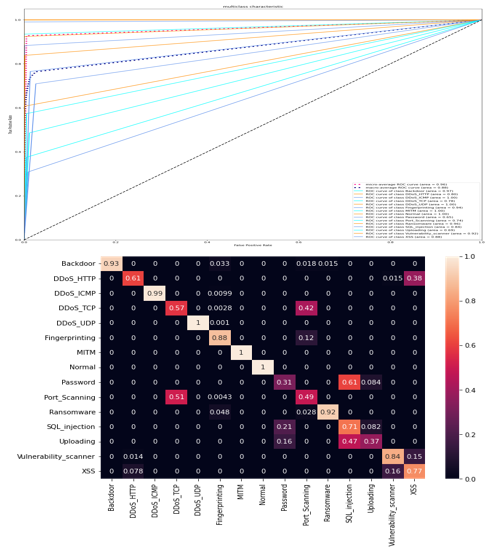
Edge computing has emerged as a promising paradigm to address the challenges of latency-sensitive applications and the exponential growth of Internet of Things (IoT) devices. However, the distributed nature of edge networks introduces new security vulnerabilities, necessitating robust intrusion detection mechanisms. In this paper, we propose EdgeGuard, a machine learning based framework for proactive intrusion detection on edge networks. Leveraging convolutional neural networks (CNNs) arranged in a residual fashion, EdgeGuard effectively captures complex patterns in network traffic data, enhancing the system's ability to detect intrusions with high accuracy. We conduct experiments using the Edge-IIoTset Cyber Security Dataset, containing a diverse range of normal and attack traffic samples. The proposed method achieves promising results, as evidenced by the receiver operating characteristic area under the curve (ROCAUC) and confusion matrix analysis. EdgeGuard offers a robust solution to safeguard edge computing environments against cyber threats, contributing to the security and integrity of IoT systems in real-world deployment scenarios.
Downloads
Article Details

This work is licensed under a Creative Commons Attribution 4.0 International License.